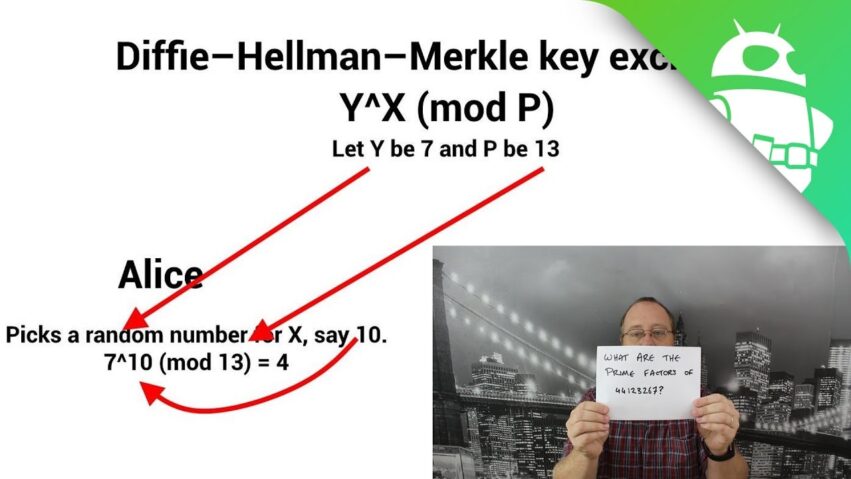
How keys are distributed is vital to any encryption system. Find out how to do it with the Diffie–Hellman key exchange and using public-key cryptography. Find out more: https://goo.gl/qI6jxZ
Download the AndroidAuthority App: https://play.google.com/store/apps/details?id=com.androidauthority.app
Subscribe to our YouTube channel: http://www.youtube.com/subscription_center?add_user=androidauthority
—————————————————-
Stay connected to Android Authority:
– http://www.androidauthority.com
– http://google.com/+androidauthority
– http://facebook.com/androidauthority/
– http://twitter.com/androidauth/
– http://instagram.com/androidauthority/
Follow the Team:
Josh Vergara: https://plus.google.com/+JoshuaVergara
Joe Hindy: https://plus.google.com/+JosephHindy
Lanh Nguyen: https://plus.google.com/+LanhNguyenFilms
Jayce Broda: https://plus.google.com/+JayceBroda
Gary Sims: https://plus.google.com/+GarySims
Kris Carlon: http://plus.google.com/+KrisCarlon
Nirave Gondhia: http://plus.google.com/+NiraveG
John Velasco: http://plus.google.com/+JohnVelasco
Bailey Stein: http://plus.google.com/+BaileyStein1












![suspect for fraud in the 6th District [VIDEO] – Blotter](https://avnblogfeed.com/wp-content/uploads/2024/04/Fraud-6xx-N-11th-St-DC-24-06-003505-100x100.jpg)






wrrr
Outstanding on public-key ….thank you much!
Ok what i'm still tripping on (Using Alice and Bob in my example) – I get that Bob's public and private key are mathematically linked. However if Alice is across the globe how is her public and private linked to Bob. So as I understand it, Bob will use his public key to encrypt a message and send to Alice which she uses her private key to decrypt. OK i'm fine with that. But how is Alices private key linked to Bobs key? If Bob wants to send another msg, say to Tom – again he uses his public key to encrypt. Tom uses his private to decrypt – how is Tom's key linked? I'm missing something super basic here. Any help appreciated
Please help me
Why is 7d x mod [(p-1) (q-1)] = 1 ===> like where did this come from?
Amazing explanation!. s the document with the detailed explanation still available somewhere? the link in the description unfortunately doesn't work (anymore).
what are some common use cases for this kind of cryptography? Is Diffie-Hellman the most widely used by all encryption applications?
Good job mate
good video. thanks.
Need a video on Digital Signatures.
After 2 minutes after I leaned RSA I got the private key from the public key using alexa
Business Opportunity in Ruvol
I have invented a Board Game [still unpublished and not yet out in the market] that I believe is guaranteed to be as challenging and exciting as CHESS. I called it “RUVOL.”
It is my hope that one day Ruvol may surpass chess as the “Number One Board Game in the World.”
The weakness of chess is it always starts in fixed positions that the opening moves become “memorizable.” In fact, not a few have so mastered the moves that they can play against their opponents “blindfolded.” It is for this very reason that the great Bobby Fischer introduced his so-called “Fischer Random Chess,” where the starting position of the pieces is “randomized” to make the memorization of openings impracticable. Fortunately, it is also for this reason that I invented Ruvol where “every game” has been calculated to be a challenging one to play.
HOW IS RUVOL PLAYED and HOW YOU CAN MONETIZE IT?
I detailed everything in my YouTube video. Here is the link: https://www.youtube.com/watch?v=jcqth0m3-R0
BIG MONEY POTENTIAL IN RUVOL!
It is worthwhile to note that the people who play chess will be the same people who will play Ruvol. In my Google search, I learned there are around 800 million chess players in the world. Even just a small percentage of these 800 million is good enough to earn big money from Ruvol either as an ONLINE GAME BUSINESS or as a PHYSICAL PRODUCT DISTRIBUTOR.
You may contact me at: rodolfovitangcol@gmail.com.
Thanks and God bless!
RODOLFO MARTIN VITANGCOL
The Ruvol Inventor
Great video
Brilliant explanation. 👍👍👍
When he said: "Here comes the magic". It truly was a magic, cause I didn't have clue how he did it!? 🙂
Great Video and the content! It took me 2 attempts to unterstand everything, and when someone asked to explain how Public and private key concept work I was stuck.
My answer was: "check it on YouTube, then we can talk about it"
Thanks for the video!!!!!!!!!!!
This is, without any doubt, the best explanation video on YouTube on this subject. Thanks a lot.
ericto0lls on instagram or whatsapp *16572076574 turns my non spendable btc into spendable. Now I've got a lot of btc. Thanks eric
erictoolls on instagram or whatsapp *16572076574 turns my non spendable btc into spendable. Now I've got a lot of btc. Thanks eric
erictoolls on instagram or whatsapp *16572076574 turns my non spendable btc into spendable. Now I've got a lot of btc. Thanks eric
I recommend erictoolls on instagram or whatsapp *16572076574 to you all to help you out cause he finds solution to every of my problems.
All thanks to LUNAPRY05 on lnsta who unlock my non spendable btc to spendable with an ACTIVE PRIVATE KEY… he’s a pr0
All thanks to LUNAPRY05 on lnsta who unlock my non spendable btc to spendable with an ACTIVE PRIVATE KEY… he’s a pr0
All thanks to LUNAPRY05 on lnsta who unlock my non spendable btc to spendable with an ACTIVE PRIVATE KEY… he’s a pr0
All thanks to LUNAPRY05 on lnsta who unlock my non spendable btc to spendable with an ACTIVE PRIVATE KEY… he’s a pr0
Try erictoolls on instagram or whatsapp *16572076574. He's an expert
have you been scammed of your bitcoins and would like to hack back your lost btc? This new software will enable you to hack any btc private key and gain access to the total funds
https://youtu.be/9Wryo8mD3do
Thank you so much! I just spent an hour searching for this example, this is the first video that actually covered the part I wanted to understand, how the data is actually manipulated. Thank you!!
Best explanation on this subject ever. I keep coming back for another look, change the numbers for ones I chose, do the math and find it always works. Trouble is, I still don't know for sure how! 😜 Thanks Garry.
since the dynamic shortened link above is broken. Here's the working one: https://www.androidauthority.com/public-key-cryptography-717863/
anyone noticed the answer 7691 X 5737 is visible @4:28 😀
This video is the answer for a lot of people.